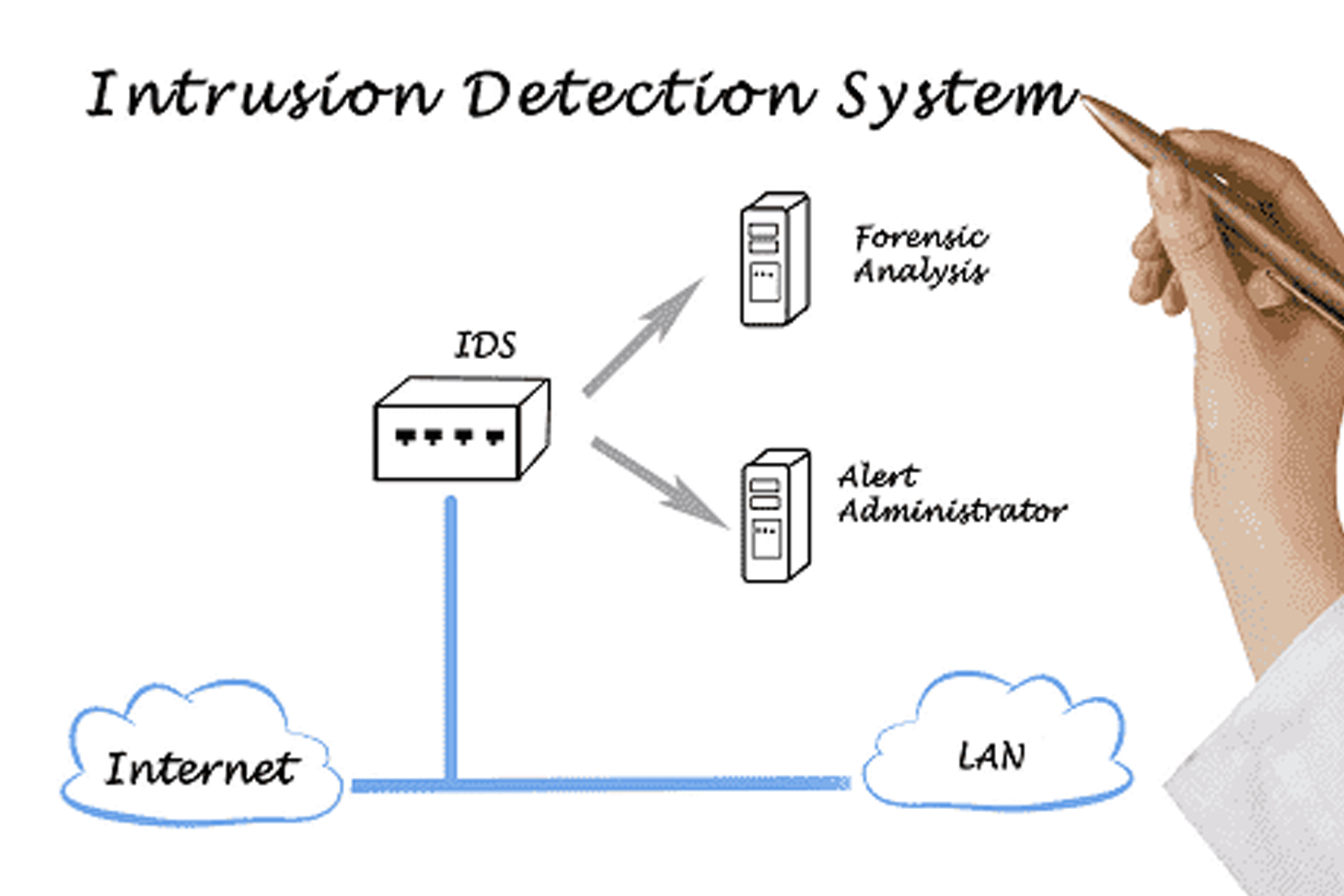
A system called an intrusion detection system (IDS) observes network traffic for malicious transactions and sends immediate alerts when it is observed. It is software that checks a network or system for malicious activities or policy violations. Each illegal activity or violation is often recorded either centrally using a SIEM system or notified to an administration. IDS monitors a network or system for malicious activity and protects a computer network from unauthorized access from users, including perhaps insiders.
An intrusion detection system (IDS) is a type of security software designed to automatically alert administrators when someone or something is trying to compromise information system through malicious activities or through security policy violations.
An IDS works by monitoring system activity through examining vulnerabilities in the system, the integrity of files and conducting an analysis of patterns based on already known attacks. It also automatically monitors the Internet to search for any of the latest threats which could result in a future attack.
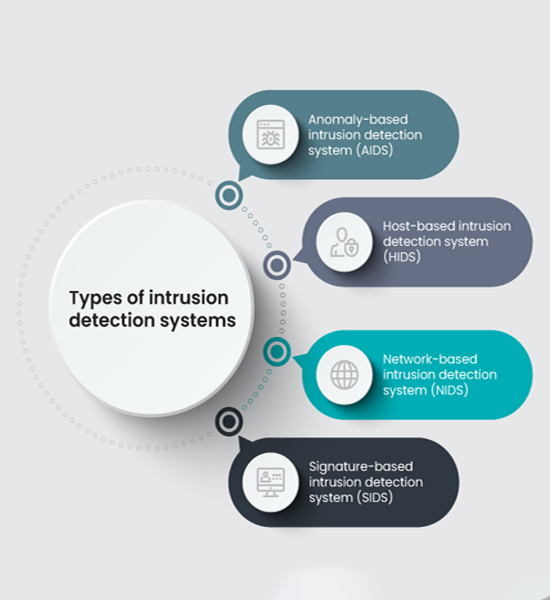
There are a multiple ways detection is performed by an IDS. In signature-based detection, a pattern or signature is compared to previous events to discover current threats. This is useful for finding already known threats, but does not help in finding unknown threats, variants of threats or hidden threats.
Another type of detection is anomaly-based detection, which compares the definition or traits of a normal action against characteristics marking the event as abnormal.


Why is having an IDS Security System important?
IDS security systems provide critical visibility into inbound and outbound network traffic by alerting admins when malicious signatures, intrusion patterns, or anomalous activity is detected. This enables technicians to immediately investigate possible threats and to prevent or mitigate the damage of cyberattacks.
The unfortunate truth is all networks are penetrable, and a comprehensive set of security tools including firewalls, anti-virus software, and IDS and IPS systems is vital to fending off and catching malicious activity. As cyberattackers devise new attack vectors and methods to take advantage of potential weaknesses or gaps in network defenses, increasingly sophisticated security systems are essential.
The Advantages of an Intrusion System

Intrusion Prevention
Our comprehensive security solutions are designed to deter intruders and protect your premises from unauthorized access. By implementing advanced technologies and proactive measures, we create a robust security system that safeguards your property.
Integrated System
Our security solutions seamlessly integrate multiple components, such as access control, video surveillance, and alarm systems, into a unified and cohesive system. This integration enhances efficiency, centralizes management, and maximizes the effectiveness of your security measures.
Tailored Solutions
We understand that each client has unique security requirements. That's why we offer individually tailored solutions to meet your specific needs. Our experts work closely with you to design a customized security system that aligns with your objectives and provides optimal protection.
Proactive Measures
We believe in taking proactive action to prevent security breaches. Our solutions include proactive monitoring, real-time alerts, and proactive response protocols to detect and address potential threats before they escalate, ensuring the safety of your premises and occupants.
Peace of Mind
With our robust security solutions in place, you can have peace of mind knowing that your property and assets are well-protected. Our comprehensive approach to security and our commitment to excellence instill confidence and assurance in our clients.
Reporting Capabilities
We provide detailed reporting capabilities that allow you to request and access comprehensive security reports. These reports provide valuable insights into system performance, incidents, and security trends, enabling you to make informed decisions and further enhance your security measures.
Products & Solutions
Magnetic Contact |
|
Motion Sensors |
|
Panic Swtich |
|
Sutter Contact |

